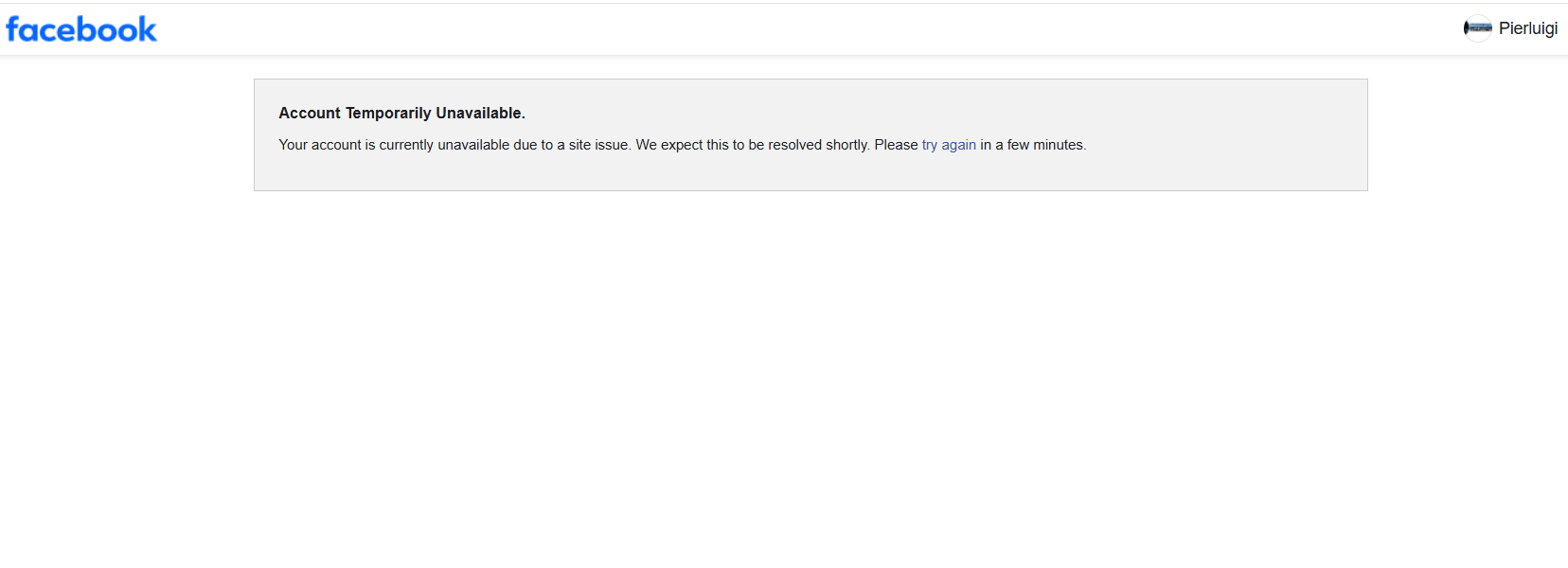
#Facebook Fails: Global Outage Sparks Security Concerns
In a shocking turn of events, social media giant Facebook has experienced a global outage affecting millions of users worldwide. The outage began at 4:15 PM ET, with users unable to access their accounts due to an unexpected site issue. Despite the company's reassurances that the problem would be resolved shortly, reports of login and website issues flooded DownDetector, a platform that tracks outages and disruptions.
The situation became even more concerning when independent internet monitors like NetBlocks reported international outages not related to country-level filtering or disruptions. This suggested that the issue was likely caused by an internal vulnerability or a malicious attack. However, despite numerous investigations, Facebook has yet to disclose the root cause of the problem.
What triggered this global outage?
The exact cause of the Facebook outage is still unknown, but experts speculate that it could be related to various factors such as:
* A malware attack: Cyber attackers often target vulnerabilities in software applications and systems. * **Data breach**: Social media platforms like Facebook have faced numerous data breaches in the past, highlighting the importance of robust security measures. * **Vulnerability exploit**: The outage may have been caused by an unpatched vulnerability in the Facebook application or its underlying infrastructure.
The impact of this outage
A global outage can have significant consequences for organizations like Facebook. The company's reputation and trust with its users are at risk, which could lead to financial losses and long-term damage.
The incident highlights the importance of:
* **Regular security updates**: Software applications and systems need regular security patches to prevent vulnerabilities. * **Cybersecurity awareness**: Companies must prioritize cybersecurity to protect their users' data and maintain trust in the digital world.
What can you do?
If you're a Facebook user, there are several steps you can take:
1. **Stay informed**: Follow official updates from Facebook and reputable sources like NetBlocks or DownDetector. 2. **Be cautious with login credentials**: Avoid sharing sensitive information online until the issue is resolved. 3. **Use alternative social media platforms**: Consider using alternative social media platforms while the outage persists.
In conclusion, the recent global outage of Facebook highlights the importance of robust security measures in the digital world. Organizations and individuals must prioritize cybersecurity to prevent similar incidents in the future.