Arduino's $61 Matter Bundle: Bringing Smart Home Harmony with Ease
The smart home space has long been plagued by fragmentation, leaving users with a plethora of devices that struggle to communicate with one another. Philips Hue bulbs and Google Home can't talk to Apple HomeKit, while Amazon Alexa is often left in the middle, confused. This issue has stymied developers and tinkerers for years, forcing them to choose between incompatible systems or work around cumbersome solutions.
Enter Matter, a universal language that brings together various smart home platforms like Apple, Google, and Amazon. Arduino, known for its DIY ethos, has now made it possible for anyone to build their own connected devices with the launch of its Matter Discovery Bundle. Priced at an affordable $61.04, this kit is designed to empower users to turn their ideas into tangible smart home creations without requiring extensive technical expertise.
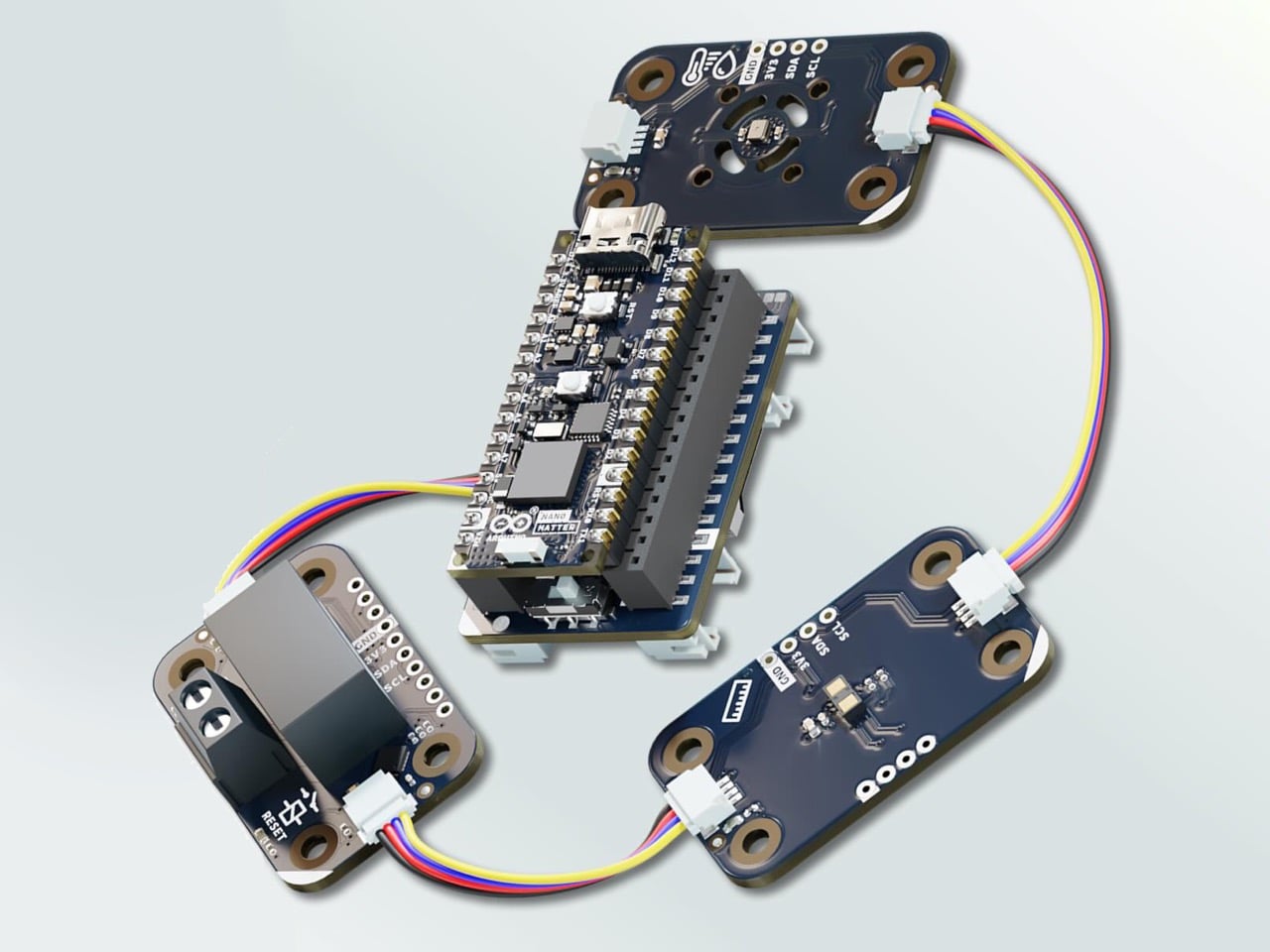
At the heart of the bundle lies the Arduino Nano Matter, a compact board that serves as the brain of your connected device. This capable little chip forms the foundation for whatever smart creation you want to build. Alongside it comes a plug-and-play connector carrier that allows you to add various components without soldering, and three sensor and control modules that cover the core building blocks of most smart home projects.
These three modules alone unlock a wide range of DIY smart devices, all of which communicate natively with Apple HomeKit, Google Home, Amazon Alexa, and Home Assistant. The presence module detects when someone is in a room using distance sensing, while another handles switching real-world appliances and devices. A third module reads temperature and humidity, providing the foundation for creating custom connected devices that fit your life rather than the other way around.
For those new to smart home development, Arduino has created a free 7-course curriculum that takes users from complete beginners to certified engineers. The course is designed to balance theory with hands-on building, allowing learners to make tangible creations as they progress. Completing the entire program earns an Arduino Certified Engineer credential, which can be valuable in product design or IoT portfolios.
The bundle was developed in collaboration with Silicon Labs, whose wireless chip technology powers the Nano Matter board at the kit's core. This enables seamless communication between devices through Arduino's Matter library, leaving users free to focus on their creative vision rather than wrestling with technical complexities.
A small caveat worth noting is that connecting your creations to a live smart home network requires a Thread border router, such as an Apple TV 4K or HomePod. Fortunately, most households are already equipped with these devices, making this minor step easily overcome.
In conclusion, Arduino's Matter Discovery Bundle offers an exciting opportunity for tinkerers and creators to build custom connected devices that fit their unique needs within existing smart home ecosystems. By reframing the smart home as a DIY space rather than a product category, this bundle has made it possible for anyone to turn ideas into reality without requiring extensive technical knowledge.