**
Dknife Toolkit Abuses Routers to Spy and Deliver Malware Since 2019
****A Powerful Linux Toolkit Used in Cyber-Espionage Attacks**
In a shocking revelation, Cisco Talos has discovered a powerful Linux toolkit called Dknife that has been used since at least 2019 to hijack router traffic and deliver malware in cyber-espionage attacks. The tool, which consists of seven Linux-based implants, performs deep-packet inspection, manipulates traffic, and delivers malware via routers and edge devices.
**
"DKnife is a fully featured gateway-monitoring and adversary-in-the-middle (AitM) framework that has been used by threat actors to spy on and control network traffic,"
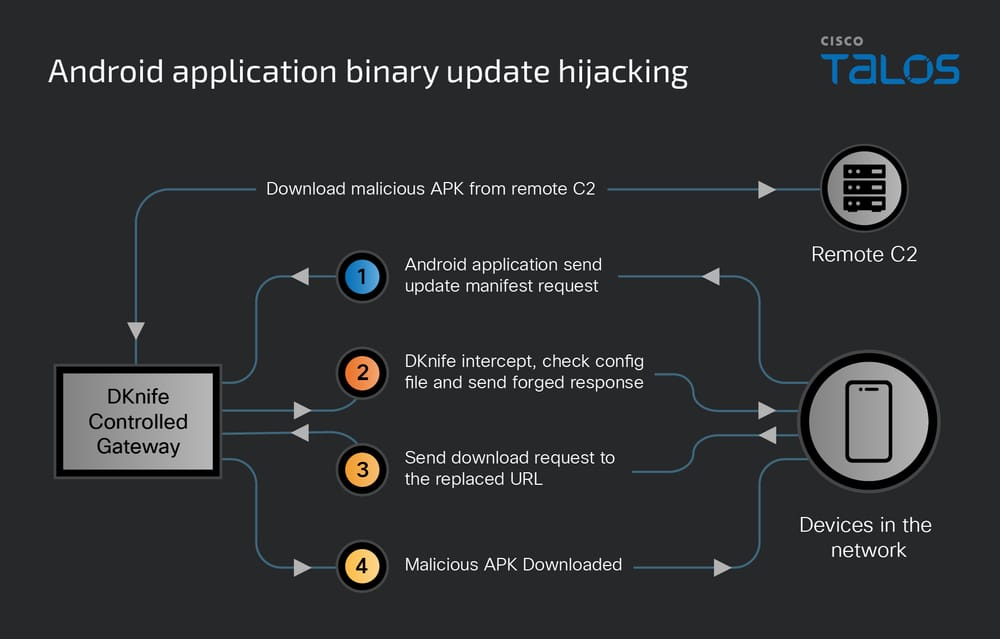
** says the report published by Talos. **"The command and control (C2) servers are still active as of January 2026."**Dknife hijacks software downloads and Android app updates to spread ShadowPad and DarkNimbus backdoors, targeting Chinese-speaking users who use popular Chinese apps like WeChat. The tool's metadata shows that attackers have used Dknife since at least 2019, with its infrastructure remaining active in January 2026.
**
Talos researchers link Dknife with high confidence to China-nexus threat actors,
** citing evidence from the toolkit's code and configuration files. "The malware collects credentials from Chinese email services and steals data from popular Chinese mobile apps and messaging platforms," says the report. **"Code and configuration files reference Chinese media domains, and attackers even hijacked Android app updates for Chinese taxi and rideshare apps."****
The framework's components are designed for routers and edge devices, particularly CentOS/RHEL systems.
** Dknife performs deep packet inspection, hijacks DNS, intercepts Android and Windows updates, disrupts security traffic, monitors users, and delivers ShadowPad and DarkNimbus backdoors. It redirects update requests to a local malicious server and replaces legitimate downloads with malware, giving attackers full control at the network edge.**
Dknife does not only hijack Android updates; it also intercepts Windows and other binary downloads to deliver ShadowPad and DarkNimbus malware.
**The tool loads encrypted hijacking rules, decrypts them with a QQ TEA-based key, and deletes them after use. When a victim downloads files like .exe or .zip, Dknife redirects the request to a malicious installer. That installer sideloads ShadowPad and DarkNimbus, then secretly connects to the attackers' real command servers.
**
The malware uses techniques and certificates linked to China-nexus threat actors.
**Dknife actively weakens security defenses and spies on users. It detects antivirus and PC-management tools like 360 Total Security and Tencent services, then blocks or disrupts their traffic to reduce protection.
**
"The DKnife traffic inspection module actively identifies and interferes with communications from antivirus and PC-management products,"
** says the report. **"It detects 360 Total Security by searching HTTP headers (e.g., the DPUname header in GET requests or the x-360-ver header in POST requests) and by matching known service domain names."**At the same time, it closely monitors user activity, tracking actions such as messaging on WeChat and Signal, shopping, reading news, map searches, gaming, dating apps, and ride-hailing. The malware also steals credentials by intercepting encrypted email connections and hosting phishing pages.
**
Researchers also found signs it may target IoT devices, and vendors are working on mitigations.
**The Dknife downloader is an ELF binary that installs and initializes the full Dknife framework on a compromised Linux device. It sets the C2 server (from a local config or a hardcoded fallback), generates a unique device ID, enables persistence at boot, downloads the Dknife package, and launches all components automatically.
**
Routers and edge devices remain prime targets in sophisticated targeted attack campaigns.
**The report concludes: **"Understanding the tools and TTPs they employ is critical."**
The discovery of the Dknife framework highlights the advanced capabilities of modern AitM threats, which blend deep-packet inspection, traffic manipulation, and customized malware delivery across a wide range of device types.
**
"Overall, the evidence suggests a well-integrated and evolving toolchain of AitM frameworks and backdoors,"
** says the report. **"This underscores the need for continuous visibility and monitoring of routers and edge infrastructure."**Follow me on Twitter: @securityaffairs and Facebook and Mastodon