Node.js Malvertising Campaign Targets Crypto Users
A malicious malvertising campaign using Node.js has been spotted targeting cryptocurrency users, according to a warning issued by Microsoft. The attack, which began in October 2024, is part of an ongoing trend of threat actors leveraging the open-source, cross-platform JavaScript runtime environment to deploy malware.
Node.js, often used for building scalable and fast web applications, has become increasingly popular among attackers due to its ability to blend malicious code with legitimate apps, bypass security tools, and persist in systems. This makes it a formidable tool for delivering info-stealing malware via fake crypto trading sites like Binance and TradingView.
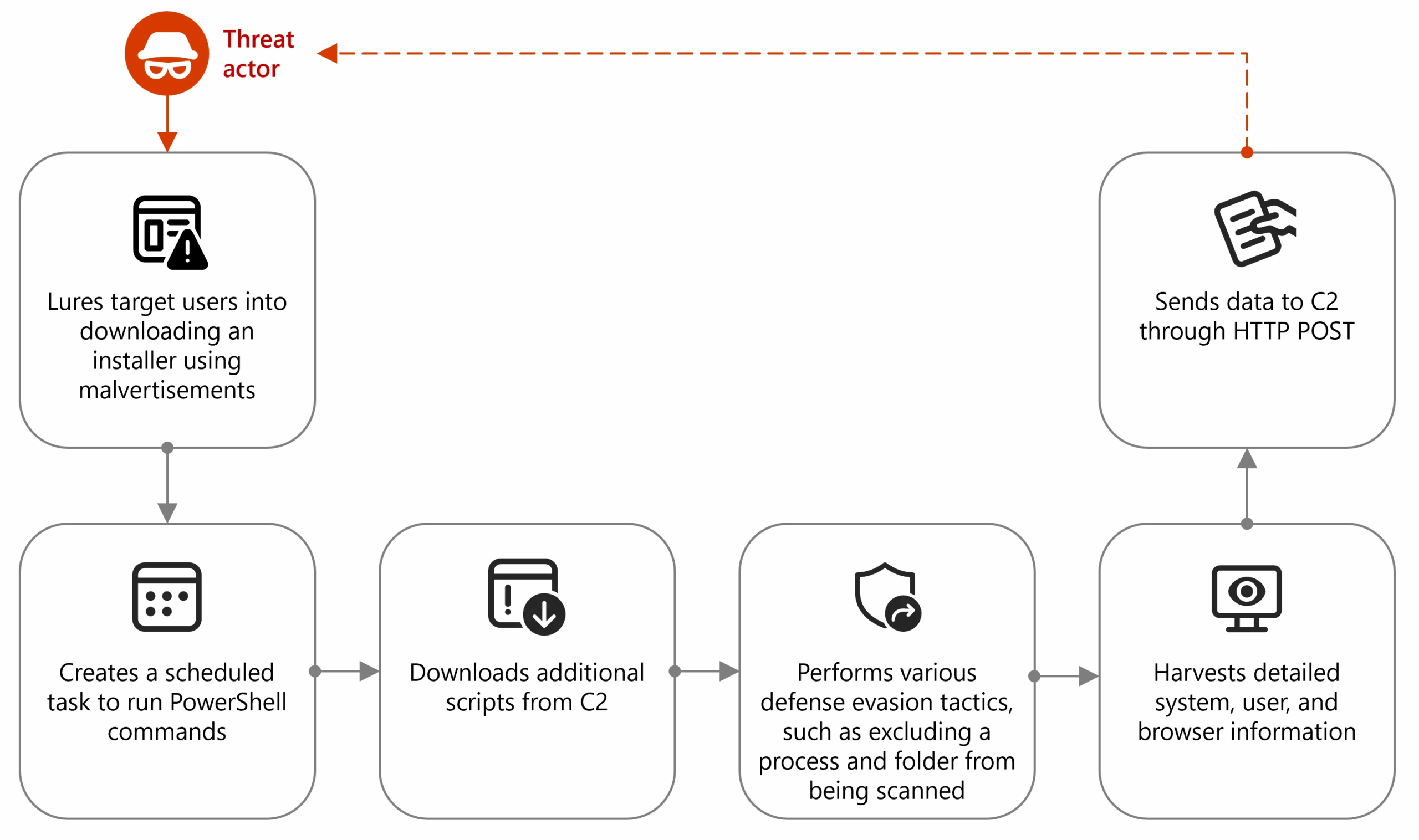
The campaign, observed by Microsoft as of April 2025, involves malvertising that lures users to fake sites offering malicious installers disguised as legitimate software. Once executed, the installer drops a malicious DLL called "CustomActions.dll" that collects system data via Windows Management Instrumentation (WMI), ensures persistence via scheduled tasks, and uses PowerShell commands for defense evasion and further payload delivery.
The attackers have employed obfuscated PowerShell scripts to fetch code from remote URLs, gather detailed system and BIOS info, package it as JSON, and send it to the attacker's Command-and-Control (C2) server. In this phase, a PowerShell script downloads an archive from the C2 server containing the Node.js runtime and a compiled JavaScript file.
Upon execution, the Node.js executable runs the script, which establishes network connections and likely extracts sensitive browser data. Another notable technique observed by researchers in recent campaigns employs inline JavaScript execution via Node.js to deploy malicious payloads.
In a documented instance, attackers used a ClickFix social engineering tactic to trick users into running a PowerShell command that downloads and installs Node.js components. The script then executes JavaScript directly through Node.js, enabling network reconnaissance, disguising command-and-control traffic as legitimate Cloudflare activity, and achieving persistence by modifying registry run keys.
Microsoft has issued a set of recommendations to mitigate threats associated with Node.js misuse. These include keeping the system up-to-date with the latest security patches, using reputable antivirus software, and being cautious when installing new software or interacting with suspicious links or attachments.
Stay Safe Online
If you're a cryptocurrency user, it's essential to be aware of these potential threats. Here are some tips to help you stay safe online:
- Keep your system and software up-to-date with the latest security patches.
- Use reputable antivirus software and ensure it's regularly updated.
- Beware of suspicious links or attachments, especially those from unknown senders.
- Be cautious when installing new software, and only download from trusted sources.
Protect Yourself with Microsoft's Recommendations
Microsoft has provided a set of recommendations to help you protect yourself from Node.js-based threats. By following these tips, you can significantly reduce the risk of falling victim to this malicious malvertising campaign:
- Enable Windows Defender for Endpoint and ensure it's configured to scan your system regularly.
- Beware of ClickFix social engineering tactics and never run suspicious PowerShell commands.
- Regularly update your browser and other software to the latest versions, and disable unnecessary plugins.
- Use a reputable security suite that includes anti-malware and anti-ransomware protection.
Stay vigilant and take these precautions seriously. By being aware of the risks and taking proactive steps to protect yourself, you can significantly reduce your chances of falling victim to this malicious malvertising campaign.