**Hackers Ruin Anti-ICE Website's Day — In Hilarious Fashion**
The website Stop ICE Raids Alert Network, a hub for anti-ICE activists to track and report ICE agents, has been breached in a cyberattack that left users with more than just a bad taste in their mouths. The hackers, who appear to be supporters of pro-ICE groups, left a parting gift on the site's front page: a message printed ominously in red letters on a black background.
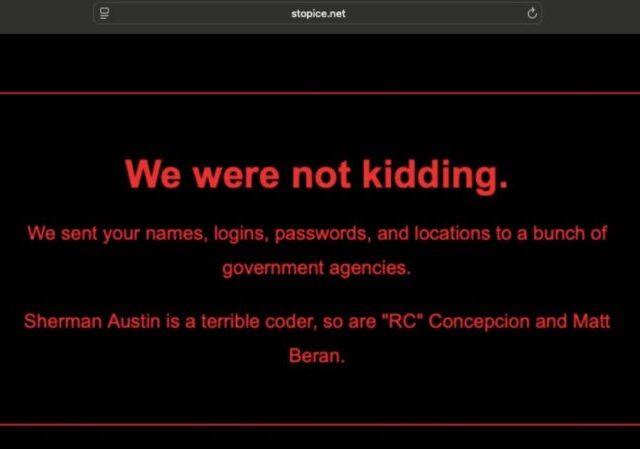
"Hello, StopICE.net. All your logins, locations, passwords, and phone numbers have been given to the FBI and ICE," the message read. "Sherman Austin is a terrible coder, so are 'RC' Concepcion and Matt Beran."
The breach was first reported by X user @DataRepublican, who posted an image of the message on Twitter along with a scathing review of the website's security measures.
BREAKING: Quick – take a look at the front page of StopICE dot net For context, StopICE is the biggest ICE doxxing website out there. Follow @astrarce and @bitchuneedsoap . pic.twitter.com/ySw3KGEWth — DataRepublican (small r) (@DataRepublican) January 30, 2026
The hackers' message was accompanied by a Tom Homan meme, which poked fun at the website's attempts to track and report ICE agents. Any attempt to search for license plates on the site triggered the meme instead of providing information.
All your logins. Locations, passwords. And phone numbers have been given to FBI and ICE. — Patriot Source Network (@PSPod25) January 29, 2026
Site administrator Sherman Austin attempted to calm users, insisting that the site was secure and asking them to "disregard the script trolls." However, his efforts were met with skepticism by anti-ICE activists, who suspected a cover-up.
Poor Sherman…. trying to tell his StopIce users there is nothing to worry about….they think you're a CBP agent…lol. @astrarce pic.twitter.com/16fqkZMhTo — GunShyMartyr (@jimmy_rustlin) January 30, 2026
The hack is seen as a major blow to anti-ICE doxxing websites, which have operated with near-total impunity for years. These sites allow users to track and report ICE agents, often using personal information such as addresses and phone numbers.
According to a Facebook post from Blue Lives Matter, efforts to expose anti-ICE doxxers are beginning to bear fruit. The group says it is hearing unconfirmed reports that conservatives who have infiltrated these agitator networks nationwide have taken evidence of their activities to some individuals' employers, resulting in several firings.
The hack also highlights the hypocrisy of anti-ICE activists, who often claim to be fighting for social justice while engaging in cyberbullying and harassment tactics. The hackers' message on the Stop ICE website was a clear indication that they are not afraid to fight back against their critics.
Hi @MikieSherrill, we can’t wait to check out the portal! https://t.co/E1pSmdRUWh — bitchuneedsoap (@bitchuneedsoap) January 30, 2026
The hack is a clear indication that pro-ICE groups are fighting back against anti-ICE activists. While some may see this as a form of cyberwarfare, it's hard to deny the effectiveness of this tactic in exposing and disrupting the activities of these websites.