Tycoon2FA Phishing Kit Rolls Out Significant Updates
The operators of the Phishing-as-a-Service (PhaaS) platform Tycoon2FA have recently rolled out significant updates to enhance its evasion capabilities. These updates are a clear indication that cybercriminals are becoming increasingly sophisticated in their tactics, making it essential for security teams to stay vigilant and adapt their defenses accordingly.
Firstly, the phishing kit has been updated to incorporate advanced evasion tactics such as a custom CAPTCHA via HTML5 canvas, invisible Unicode in obfuscated JavaScript, and anti-debugging scripts. These updates aim to bypass detection and hinder analysis by making it difficult for security software to identify the malicious activity.
A Clever Obfuscation Technique
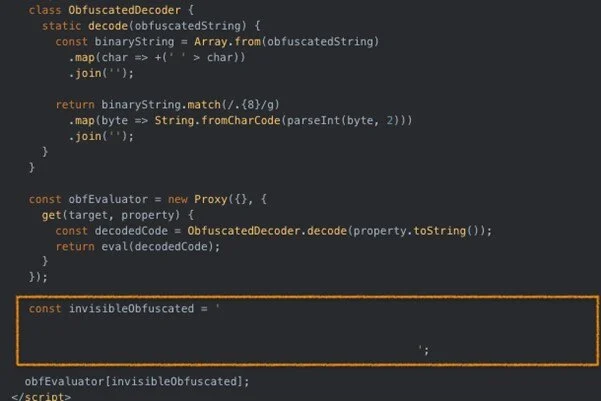
One of the most interesting updates is the incorporation of a clever obfuscation technique using invisible Unicode characters. According to Trustwave, this technique, when paired with JavaScript Proxy objects, complicate static analysis and defer script execution until runtime.
To illustrate this, Trustwave has shared a real-world example of a Tycoon 2FA phishing landing page, which can be viewed on Urlscan.io: https://urlscan.io/result/0195c73f-bfd0-7000-8386-94b11ace6088/dom/
A Custom HTML5 Canvas-Based Solution
The Tycoon 2FA phishing kit has also replaced third-party CAPTCHAs with a custom HTML5 canvas-based solution. This improvement allows for evading detection, reduces fingerprinting, and hinders automated analysis using randomized text, noise, and distortions.
Anti-Debugging Scripts
Another update is the inclusion of anti-debugging scripts to block dev tools, detect automation, prevent right-click, and spot paused execution. If analysis is suspected, these scripts redirect the user to rakuten.com, boosting evasion and extending phishing campaign lifespans.
A Clear Move Toward Stealth and Evasion
The recent updates to the Tycoon 2FA kit show a clear move toward stealth and evasion. While none of these techniques are groundbreaking individually, their combined use can complicate detection and response.
As Trustwave concludes, security teams should consider behavior-based monitoring, browser sandboxing, and a deeper inspection of JavaScript patterns to stay ahead of these tactics. The ongoing cat-and-mouse game between cybercriminals and cybersecurity professionals will continue, and it is essential that we remain vigilant and adapt our defenses accordingly.
Stay informed about the latest security threats by following me on Twitter: @securityaffairs and Facebook and Mastodon.