**Nation-state and Criminal Actors Leverage WinRAR Flaw in Attacks**
The cybersecurity community has been dealt a stark reminder of the dangers posed by zero-day vulnerabilities, as multiple nation-state and criminal actors have exploited a recently patched critical flaw in WinRAR to gain initial access and deliver malicious payloads.
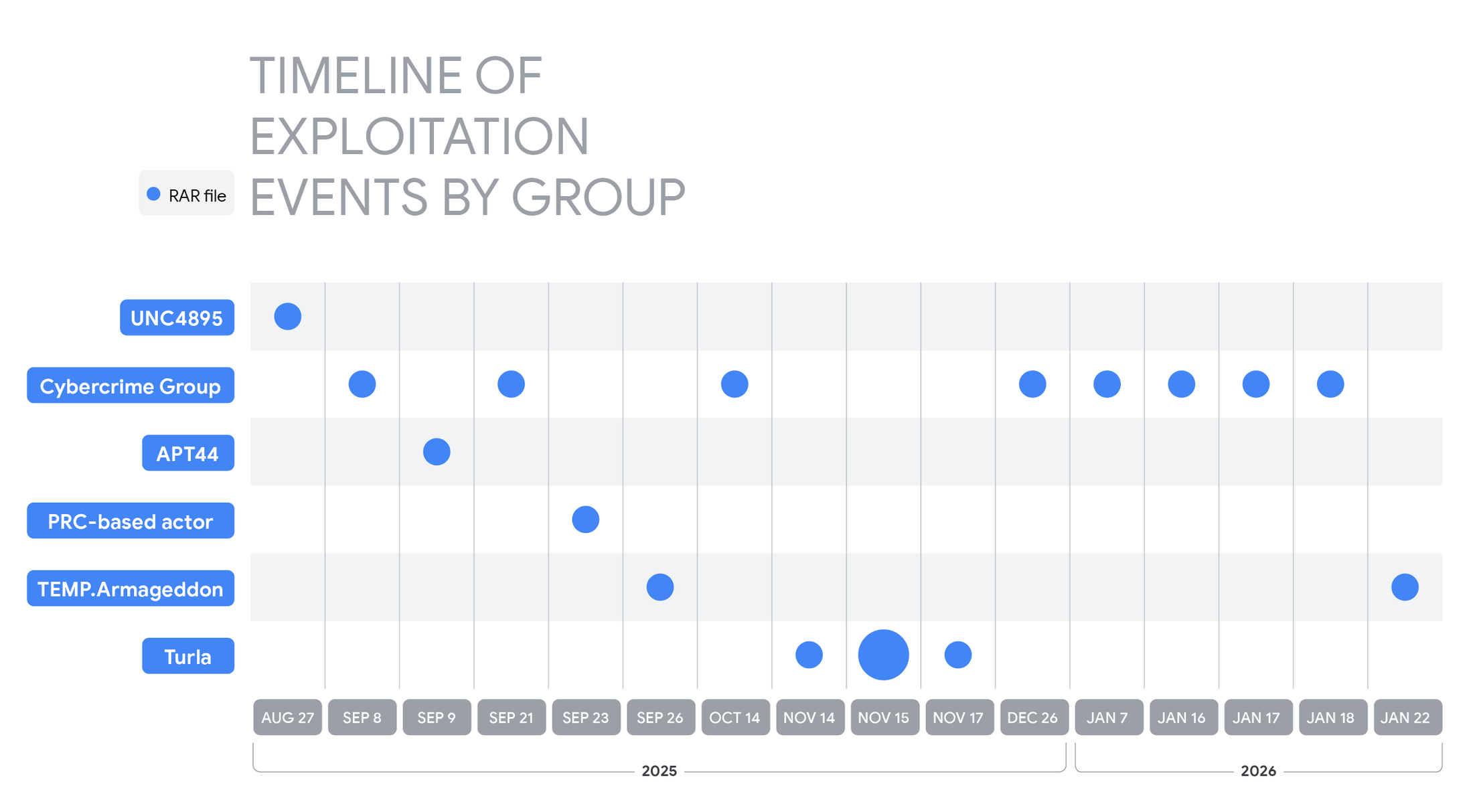
According to a report published by Google Threat Intelligence Group (GTIG), threat actors including Advanced Persistent Threats (APTs) and financially motivated groups have been actively exploiting the CVE-2025-8088 flaw in RARLAB's popular file archiver tool for Windows. The vulnerability, which affects the Windows version of WinRAR, is a directory traversal bug that allows attackers to execute arbitrary code by crafting malicious archive files.
The researchers at ESET who discovered the flaw, Anton Cherepanov, Peter Košinár, and Peter Strýček, revealed that attackers can craft archives that place executables in Windows Startup folders, causing them to run at login and enabling remote code execution. This vulnerability was exploited as a zero-day in phishing attacks to deliver RomCom malware.
The report highlights the widespread and opportunistic exploitation of CVE-2025-8088 by various threat actors, including nation-state actors linked to Russia and China, as well as financially motivated groups. These actors have used tailored lures to deliver malware such as NESTPACKER, STOCKSTAY, and multi-stage downloaders via malicious RAR archives.
Chinese actors have also been observed abusing the flaw to deploy POISONIVY, while cybercriminal groups have adopted the exploit to spread commodity RATs, stealers, and phishing tools against businesses, hospitality firms, banks, and regional users across LATAM and Asia. Activity continued into early 2026.
The report notes that this fast and broad adoption ties to the underground exploit market, where sellers like "zeroplayer" offer ready-made exploits for sale, making attacks easier for both state and criminal groups. This has turned cyberattacks into an off-the-shelf commodity.
The GTIG report concludes: "The widespread and opportunistic exploitation of CVE-2025-8088 by a wide range of threat actors underscores its proven reliability as a commodity initial access vector. It also serves as a stark reminder of the enduring danger posed by n-day vulnerabilities."
As the cybersecurity landscape continues to evolve, it is clear that nation-state and criminal actors will continue to leverage zero-day vulnerabilities like CVE-2025-8088 to gain initial access and deliver malicious payloads.
**Related Links:**
* [Google Threat Intelligence Group Report](link) * [ESET Research Paper on CVE-2025-8088](link)
**Follow me on Twitter:** @securityaffairs
**Subscribe to our newsletter:** [subscribe link]
**Connect with us on Facebook and Mastodon:** [Facebook and Mastodon links]