**Critical SmarterMail Vulnerability Under Attack, No CVE Assigned Yet**
Just days after its January 15 patch, a critical flaw in SmarterMail has been discovered to be under active attack. The issue, tracked as WT-2026-0001, lacks a CVE and was fixed with Build 9511 on January 15, 2026, following responsible disclosure by watchTowr Labs.
SmarterTools' SmarterMail is a commercial email server software designed for businesses and service providers. It provides enterprise-level email, calendar, contacts, tasks, and collaboration features. The flaw in question is an authentication bypass that allows attackers to reset the SmarterMail administrator password via a specially crafted request to the force-reset-password API endpoint.
The vulnerability lies in SmarterMail's APT unauthenticated ForceResetPassword, which trusts an IsSysAdmin flag. According to the report published by Watchtowr, "You may notice that this API endpoint accepts the ForceResetPasswordInputs object, which can be deserialized from the JSON." The researchers pointed out that this combination is unusual and typically relies on a second factor or out-of-band proof of control.
By setting it to true, an attacker can reset an administrator's password via a crafted HTTP request, gaining admin access. This bypass can then be escalated to remote code execution by abusing built-in admin features to run arbitrary OS commands, leading to SYSTEM-level access.
The researchers noted that there are no security controls in place for this API endpoint, including authentication, authorization, or verification of the old password. "Ironically, the regular user password reset flow does validate the existing password," they pointed out. "The privileged path does not."
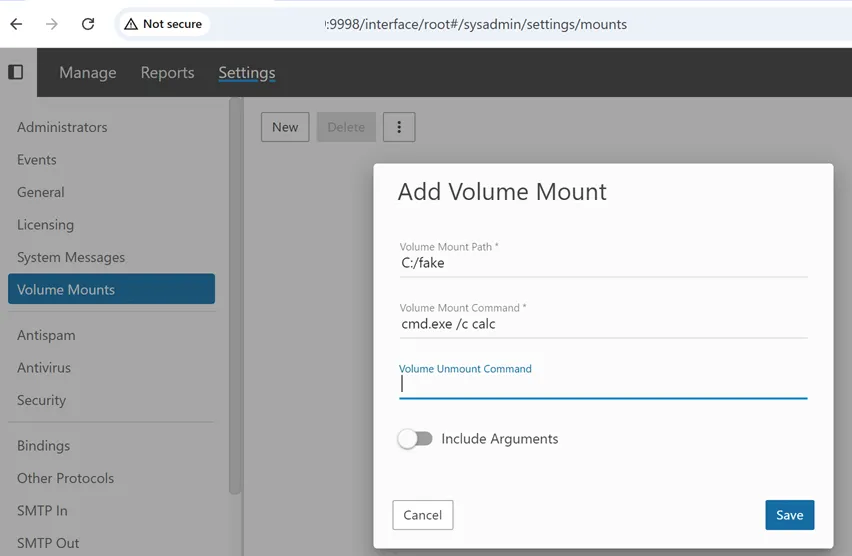
Although classified as an authentication bypass, the SmarterMail flaw enables full remote code execution. After gaining system admin access, attackers can use the Volume Mounts feature to run arbitrary OS commands, achieving SYSTEM-level control. The researchers created a proof of concept that allows achieving a SYSTEM-level shell on the target host.
The issue was patched in version 9511 on January 15, 2026, but is still actively exploited. On patched systems, exploit attempts fail due to added password validation checks. No CVE has been assigned yet.
"Given that this vulnerability is already under active exploitation," the researchers concluded, "upgrading is not optional."
**Recommendations**
* Upgrade to the latest version of SmarterMail (Build 9511 or later) * Apply patches and security updates regularly * Monitor system logs for suspicious activity
**Stay Informed**
Follow me on Twitter: @securityaffairs and Facebook and Mastodon for the latest security news and updates.