**VoidLink: The AI-Powered Linux Malware That Shows How One Developer Can Build a Powerful Threat**
The cybersecurity landscape has witnessed numerous threats over the years, but none as alarming as the recent discovery of VoidLink, a cloud-focused Linux malware framework that was likely built by a single developer using an AI model. Check Point researchers uncovered VoidLink and revealed how it poses a significant threat to organizations and individuals alike.
VoidLink is a highly mature Linux malware that rapidly evolved into a full modular framework with rootkits, cloud and container attack modules. Despite planning documents suggesting a large team was involved in its development, leaks and timelines revealed AI-generated blueprints as the primary driving force behind VoidLink's creation.
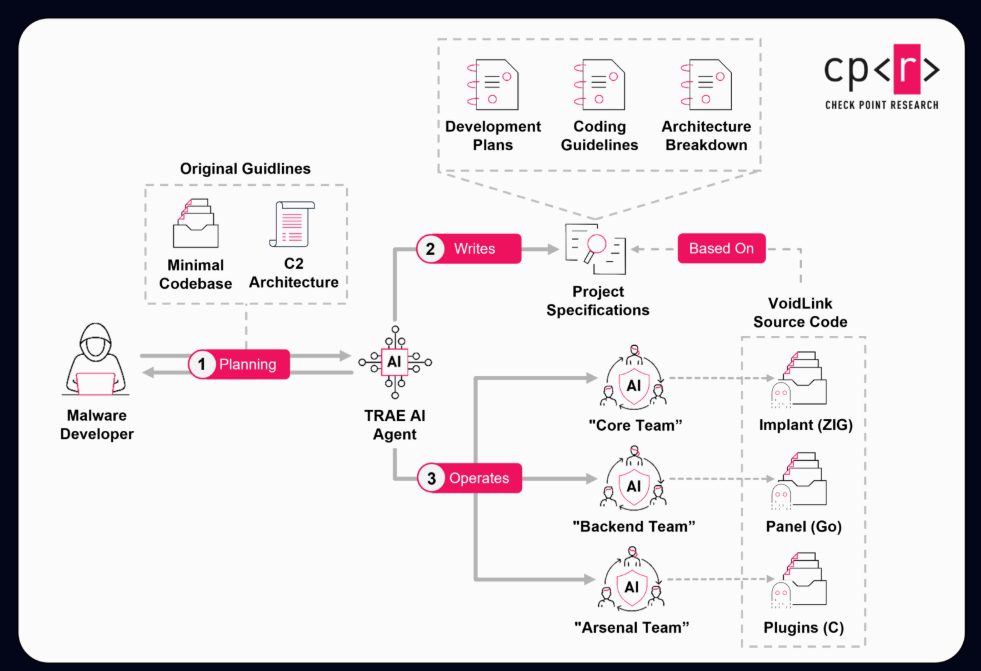
The developer, who likely used an AI agent to design the architecture, split work across three virtual teams, and generate detailed plans, coding standards, and sprints, achieved a first functional implant in under a week. This demonstrates how AI can quickly enable advanced malware development even with minimal expertise.
According to Check Point, the developer first defined goals and constraints, then used an AI agent to design the architecture. The leaked files show extensive Chinese-language documentation, timelines, and guidelines that closely match the recovered source code. Although the plans described a 20-30 week effort, evidence shows VoidLink became fully functional in under a week, reaching over 88,000 lines of code.
The case highlights how a single actor, guided by AI-generated specifications and planning, can rapidly build complex, high-quality malware. VoidLink's development likely began in late November 2025, when its developer turned to TRAE SOLO, an AI assistant embedded in TRAE, an AI-centric IDE.
While we do not have access to the full conversation history, TRAE automatically produces helper files that preserve key portions of the original guidance provided to the model. Those TRAE-generated files appear to have been copied alongside the source code to the threat actor's server, and later surfaced due to an exposed open directory.
This leakage gave us unusually direct visibility into the project's earliest directives. The leaked specs and sprints in the same TRAE IDE workflow allowed researchers to recreate VoidLink by feeding the markdown documentation to an AI model sprint by sprint. By doing so, they generated code that closely matched the real framework.
Check Point confirmed that detailed guidelines and tests limited interpretation, allowing them to reproduce the results. Each sprint produced working code that could be committed and refined, with the developer acting as product owner. This approach offloaded most coding to AI and enabled rapid progress, mirroring the output of multiple professional teams.
"Until now, solid evidence of AI-generated malware has primarily been linked to inexperienced threat actors, as in the case of FunkSec, or to malware that largely mirrored the functionality of existing open-source malware tools. VoidLink is the first evidence-based case that shows how dangerous AI can become in the hands of more capable malware developers," reads the report published by Check Point.
While not a fully AI-orchestrated attack, VoidLink demonstrates that the long-awaited era of sophisticated AI-generated malware has likely begun. In the hands of individual experienced threat actors or malware developers, AI can build sophisticated, stealthy, and stable malware frameworks that resemble those created by sophisticated and experienced threat groups.
The discovery of VoidLink serves as a warning to organizations and individuals alike to be vigilant about the evolving nature of cyber threats. As the use of AI in malware development becomes more prevalent, it is essential to stay ahead of the curve and invest in robust cybersecurity measures to protect against such sophisticated attacks.